Introduction
Terraform Native Service enables you to deploy and manage Terraform or OpenTofu infrastructure code directly within Qovery. This service type allows you to provision cloud resources, configure external services, and manage infrastructure as code (IaC) using the same environment structure as your applications. Terraform executes within Kubernetes pods on your cluster, with automatic state management, variable injection, and integrated deployment workflows.Demo: Deploy S3 and Connect to Qovery Services
Watch this interactive demo to see how to deploy S3 infrastructure using Terraform and connect it to services deployed with Qovery:Creating a Terraform Service
Open Environment Overview
Navigate to the environment where you want to deploy your Terraform infrastructure.
Configure Service Name
Provide a service name that identifies this Terraform service (e.g.,
aws-infrastructure, cloudflare-config).Select Git Repository
Choose the Git repository containing your Terraform code. This repository must include your
.tf configuration files.Specify the branch and root path if your Terraform code is in a subdirectory.Select Engine
Choose the execution engine:
- Terraform - Official HashiCorp Terraform
- OpenTofu - Open-source Terraform fork
Select Terraform Version
Choose the Terraform version to use for execution. Supported versions depend on your selected engine.
State Management
Configure how Terraform stores and manages state files. Qovery supports two state management modes.
- Default (Cluster-Managed)
- Custom Backend (AWS S3)
By default, Terraform state is managed inside the Kubernetes cluster. State files are stored securely within the cluster and managed automatically by Qovery.This default configuration requires no additional setup and is ideal for getting started quickly.Benefits:
- Zero configuration required
- Automatic state management
- Secure storage within your cluster
- No external dependencies
Execution Timeout (Default)
The default timeout is set to 1 hour. This can be customized if your Terraform operations require more time.
Cloud Credentials (Default Behavior)
By default, Terraform uses cluster credentials when provisioning resources on the same cloud provider as your cluster.If you need to use custom credentials (e.g., a different AWS account, GCP project, or Azure subscription), you will configure them in the Environment Variables step.
Compute Resources (Default)
Terraform execution uses the following default compute resources:
- CPU: 500,000 millicores (500 mCPU or 0.5 vCPU)
- Memory: 512 MB
- Storage: 1 GB
Configure Terraform Variables
Qovery provides comprehensive variable management for Terraform, automatically detecting variables from your code and allowing flexible configuration.Automatic Variable DetectionQovery automatically loads variables from:Qovery will create:Manual Variable OverrideYou can manually override any variable value in two ways: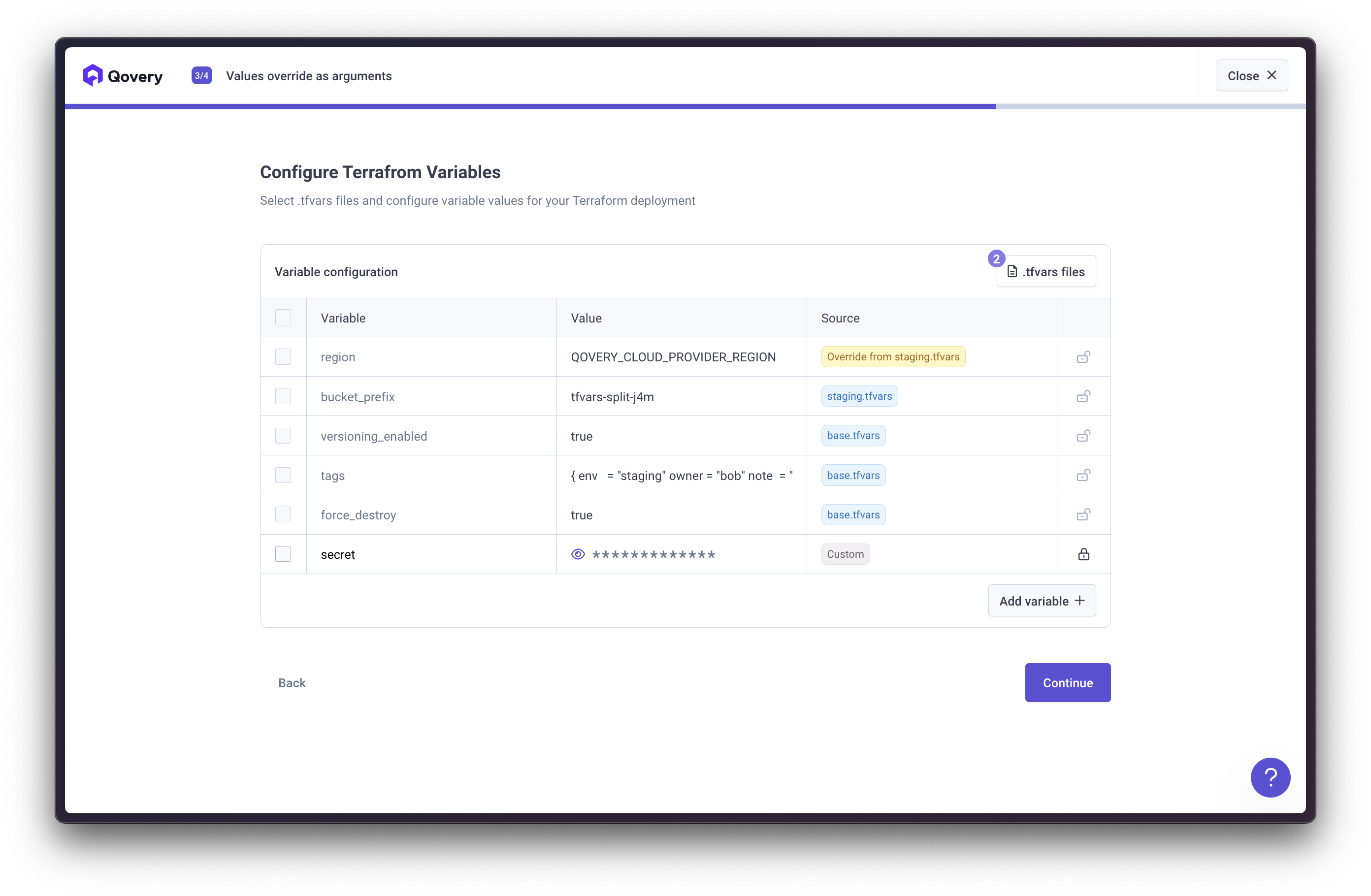
main.tfvariables.tf
tf_var_.Example:If your variables.tf contains:tf_var_bucket_nametf_var_environment
.tfvars files to configure multiple variables at once:- Click Import TFVAR
- Select the TFVAR file(s) to import
- Choose which TFVAR files to apply
- Reorder the TFVAR files as needed
The last TFVAR file applied wins. If multiple TFVAR files define the same variable, the value from the last file in the order takes precedence.
-
Direct Value Entry - Enter a value directly:
-
Reference Environment Variable - Reference another environment variable:
.tf files that are not in main.tf or variables.tf, Qovery will not automatically detect them. You can create these variables manually using the tf_var_ prefix:
Configure Environment Variables
Add standard environment variables that will be available during Terraform execution. This is where you configure custom cloud provider credentials, provider-specific settings, and other configuration.Common use cases:Custom Cloud CredentialsOverride the default cluster credentials with your own:AWS:GCP:Azure:Provider ConfigurationAdd provider-specific environment variables:Cloudflare:Datadog:Terraform Environment VariablesYou can also set Terraform-specific environment variables:
Running Terraform
After creating your Terraform service, you can execute Terraform commands using the Action Toolbar.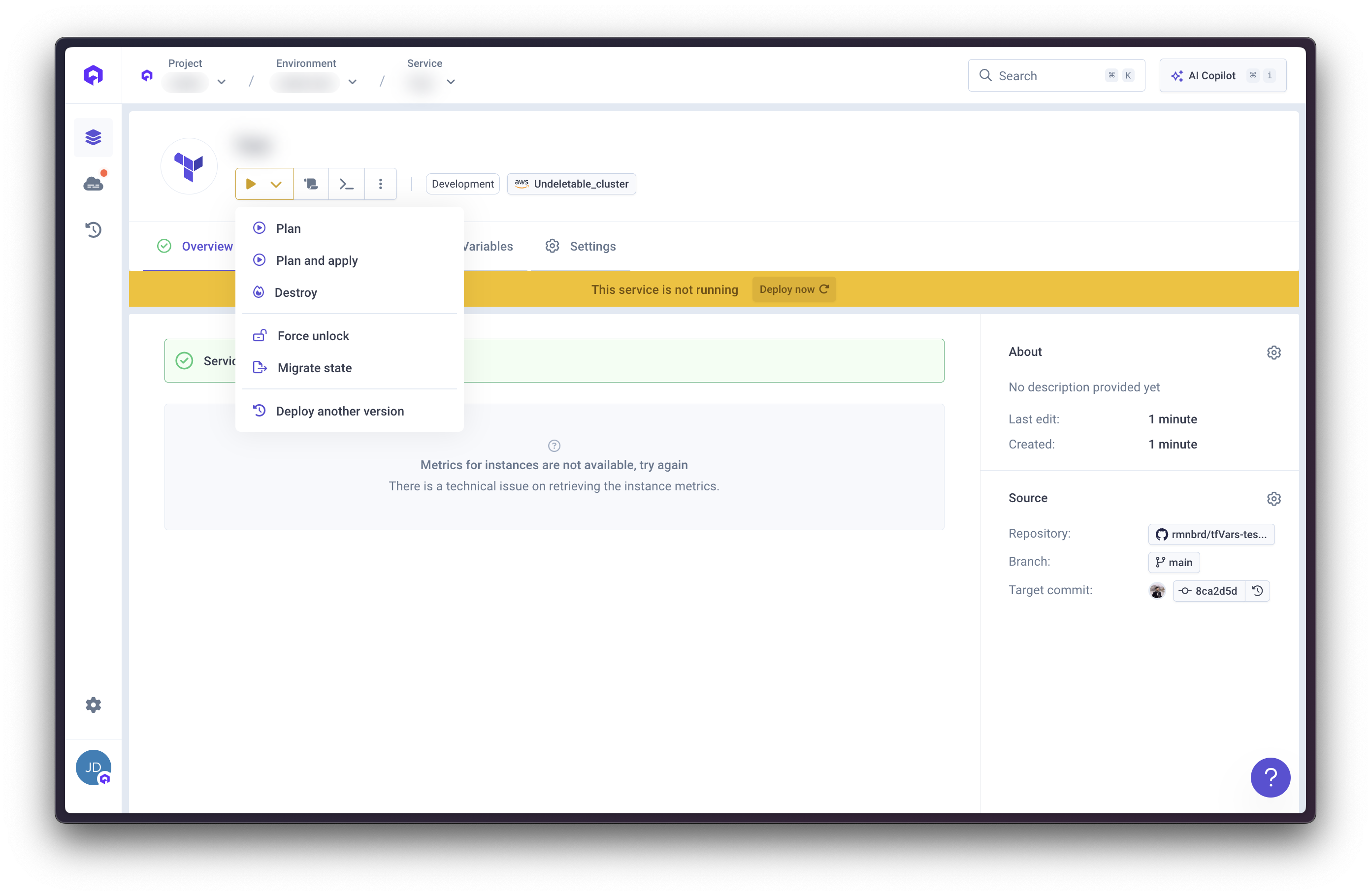
Available Actions
The following Terraform operations are available from the service’s Action Toolbar:Plan
Plan
Executes
terraform plan to preview infrastructure changes without applying them.Use this to:- Review what Terraform will create, modify, or destroy
- Validate your Terraform configuration
- Check for drift between your code and actual infrastructure
Plan & Apply
Plan & Apply
Executes
terraform plan followed by terraform apply to provision or update infrastructure.This is the standard deployment action that:- Generates an execution plan
- Applies changes to your infrastructure
- Updates the Terraform state
Destroy
Destroy
Executes
terraform destroy to remove all resources managed by this Terraform service.Force Unlock
Force Unlock
Releases a stuck Terraform state lock.Use this if:
- A previous Terraform operation was interrupted
- State is locked and preventing new operations
- You see “state is locked” errors
Migrate State
Migrate State
Migrates Terraform state between storage backends or updates state schema.This operation runs
terraform init -migrate-state to:- Move state to a new backend
- Upgrade state file format
- Reconfigure state storage
Create & Run Plan
During service creation, you can select Create & Run Plan to immediately executeterraform plan after the service is created.
This allows you to:
- Preview infrastructure changes before deployment
- Validate your Terraform configuration
- Review the execution plan before committing to apply
Terraform Service Settings
After creating your Terraform service, you can update all configuration options in the Service Settings.General Configuration
All parameters from the creation flow can be modified:Git Repository
Git Repository
- Change the Git repository source
- Update the branch to deploy from
- Modify the root path for Terraform code location
Engine
Engine
- Switch between Terraform and OpenTofu
- This change will take effect on the next deployment
Version
Version
- Update the Terraform or OpenTofu version
- Useful for testing new versions or maintaining compatibility
State Management
State Management
- Modify state storage configuration
- Update state backend settings if using custom backend
Timeout
Timeout
- Adjust the execution timeout (default: 1 hour)
- Increase for long-running Terraform operations
- Decrease to fail faster for quick validations
Execution Resources
Execution Resources
- Update CPU allocation (default: 500 mCPU)
- Modify memory allocation (default: 512 MB)
- Adjust storage allocation (default: 1 GB)
- Manage a large number of resources
- Require significant memory for state processing
- Need more CPU for provider operations
Environment Variables
Environment Variables
- Add or update cloud provider credentials
- Configure Terraform input variables (
TF_VAR_*) - Set provider-specific environment variables
- Reference secrets for sensitive values
Terraform Arguments
The Terraform Arguments section allows you to specify additional CLI arguments for each Terraform command. These arguments override default behaviors and enable advanced customization.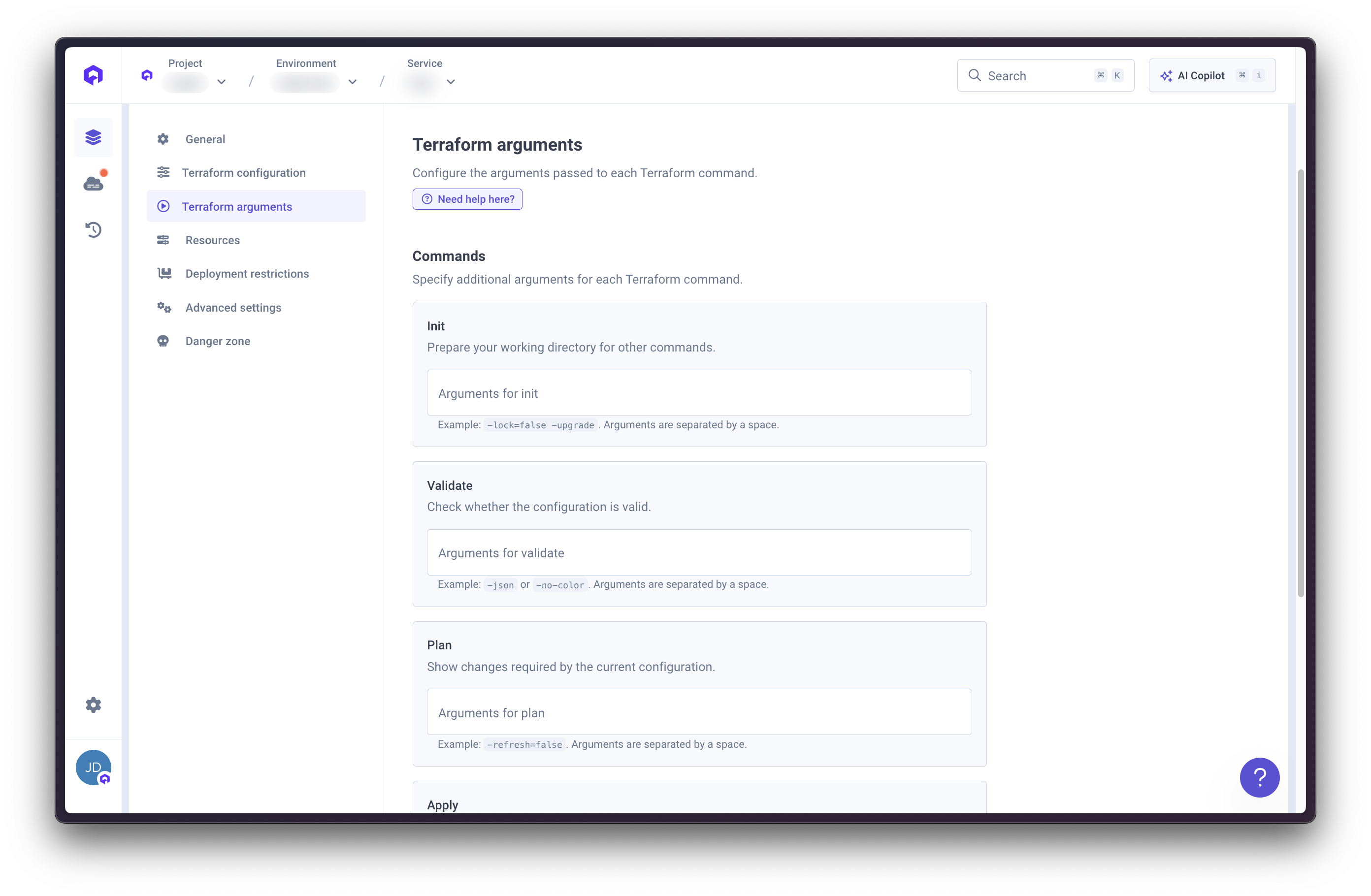
Terraform Arguments provide fine-grained control over Terraform execution. Use these to customize init, validate, plan, apply, and destroy operations.
Init Arguments
Init Arguments
Customize
terraform init behavior.Common arguments:-upgrade- Upgrade modules and providers to latest versions-reconfigure- Reconfigure backend ignoring existing configuration-backend-config=...- Override backend configuration
Validate Arguments
Validate Arguments
Customize
terraform validate behavior.Common arguments:-json- Output validation results in JSON format-no-color- Disable colored output
Plan Arguments
Plan Arguments
Customize
terraform plan behavior.Common arguments:-target=resource.name- Plan changes for specific resource only-var="key=value"- Set a variable value-var-file=filename- Load variables from file-out=filename- Save plan to a file-refresh=false- Skip state refresh-parallelism=n- Limit concurrent operations
Apply Arguments
Apply Arguments
Customize
terraform apply behavior.Common arguments:-target=resource.name- Apply changes to specific resource only-var="key=value"- Set a variable value-var-file=filename- Load variables from file-parallelism=n- Limit concurrent operations-refresh=false- Skip state refresh
Destroy Arguments
Destroy Arguments
Customize
terraform destroy behavior.Common arguments:-target=resource.name- Destroy specific resource only-var="key=value"- Set a variable value-parallelism=n- Limit concurrent operations-refresh=false- Skip state refresh
- Separate multiple arguments with spaces
- Quote values containing spaces:
-var="name=my value" - Use multiple
-varflags for multiple variables:-var="a=1" -var="b=2"
Custom Build Image
By default, Terraform services run using a base Docker image (Debian-based) containing Terraform (or OpenTofu),dumb-init, rsync, bash, and ca-certificates. If your Terraform code requires additional binaries or tools (e.g., AWS CLI, kubectl, jq, custom scripts), you can customize the build image using a Dockerfile fragment.
Configuring a Dockerfile Fragment
Qovery provides two ways to inject custom Dockerfile commands during the build:- File-based: Reference a Dockerfile fragment file stored in your Git repository
- Inline: Provide Dockerfile commands directly in the service configuration
- File-based Fragment
- Inline Fragment
Reference a Dockerfile fragment file from your repository.
Create Fragment File
In your Git repository, create a Dockerfile fragment file in your Terraform code directory or a custom location.Example directory structure:
Add Dockerfile Instructions
Add valid Dockerfile instructions to install the tools you need. The fragment is injected into the build after your Terraform files are copied and before the final user switch.See the Fragment Examples section below for common use cases.
Configure Service
In the Terraform service settings, configure the Dockerfile fragment:
- Navigate to Service Settings → Dockerfile Fragment
- Select Custom file path
- Enter the absolute path to your fragment file (e.g.,
/terraform/custom-build.dockerfile)
The path must be absolute (starting with
/) and located within your service’s root_path.Fragment Examples
Installing AWS CLI and common tools:Supported Dockerfile Instructions
The fragment supports the following Dockerfile instructions:RUN- Execute commands during build (install packages, configure tools, etc.)ADD- Add files with URL/archive support (download and extract remote archives)
Repository files are already present in
/data before the fragment executes, so you can reference them in RUN commands without needing COPY.This feature is specific to Terraform and OpenTofu services. Applications and Jobs use different build mechanisms.
Clone Service
You can create a clone of the service via the clone feature. A new service with the same configuration will be created into the target environment.The target environment can be the same as the current environment or a different one in a completely different project.

