Overview
On your first sign in to the Qovery Console, you need to login via your Git provider account (GitHub, GitLab, or Bitbucket). This allows Qovery to manage your repositories and create webhooks to track push events and pull requests for auto-deployment and preview environments. Qovery offers two approaches for Git repository access:- User-based access (default): Uses your personal Git provider login
- Git tokens (recommended): Centralized token management for decoupled permission control
Legacy GitHub App: The Qovery GitHub App is being deprecated and will be replaced by the Git tokens system. Existing users should migrate to tokens for better flexibility and control.
Git Tokens
Git tokens enable centralized management of Git repository access. Tokens are created within your Git provider and added to your Qovery organization, decoupling permissions from individual user accounts.Managing Tokens on Git Provider
Create tokens in your Git provider with the appropriate permissions:GitHub
GitHub supports two token types:- Personal Access Tokens (Classic)
- Fine-Grained Personal Access Tokens
Classic tokens provide full control with simpler configuration.Required Permissions:
repo(Full control of private repositories) - Requiredadmin:repo_hook(Full control of repository hooks) - Requiredread:org(Read org and team membership) - if using GitHub organizations
- Go to GitHub Token Settings
- Click Generate new token (classic)
- Add a descriptive note (e.g., “Qovery Access”)
- Select the required scopes above
- Choose an expiration period
- Click Generate token and copy immediately
GitHub vs GitHub Enterprise
When adding a GitHub token in Qovery:- GitHub (Cloud)
- GitHub Enterprise
Use this option for repositories hosted on github.com:
- No additional configuration needed
- Uses standard GitHub.com API
- Default option for most users
GitLab
GitLab supports project, group, and personal access tokens.- Project Tokens
- Group Tokens
For access to specific projects:Required Configuration:
- Role: Maintainer or Owner
- Scopes:
api(Access the API) - Requiredread_repository(Read access to repositories) - Required
- Go to your GitLab project > Settings > Access Tokens
- Click Add new token
- Enter token name and expiration date
- Select Maintainer or Owner role
- Check required scopes
- Click Create project access token and copy immediately
GitLab.com vs Self-hosted
When adding a GitLab token in Qovery:- GitLab.com: No additional configuration needed
- Self-hosted GitLab: Provide your GitLab server URL (e.g.,
https://gitlab.company.com)
Ensure your self-hosted GitLab instance is accessible from Qovery.
Bitbucket
Bitbucket supports repository and workspace access tokens.- Repository Access Tokens
- Workspace Access Tokens
For access to specific repositories:Required Permissions:
- Repositories: Read - Required
- Pull requests: Read and write - Required
- Webhooks: Read and write - Required
- Go to repository > Repository settings > Access tokens
- Click Create Repository Access Token
- Enter token name and expiration
- Select required permissions
- Click Create and copy immediately
Token Expiration
Git provider tokens typically include expiration dates. To maintain continuous repository access:- Monitor expiration: Check your Git provider settings regularly
- Renew before expiry: Either extend expiration (if supported) or generate a new token
- Update in Qovery: Replace the old token value in Qovery organization settings
- Verify connection: Test with a deployment
- Revoke old token: Delete the old token from your Git provider
Managing Tokens on Qovery
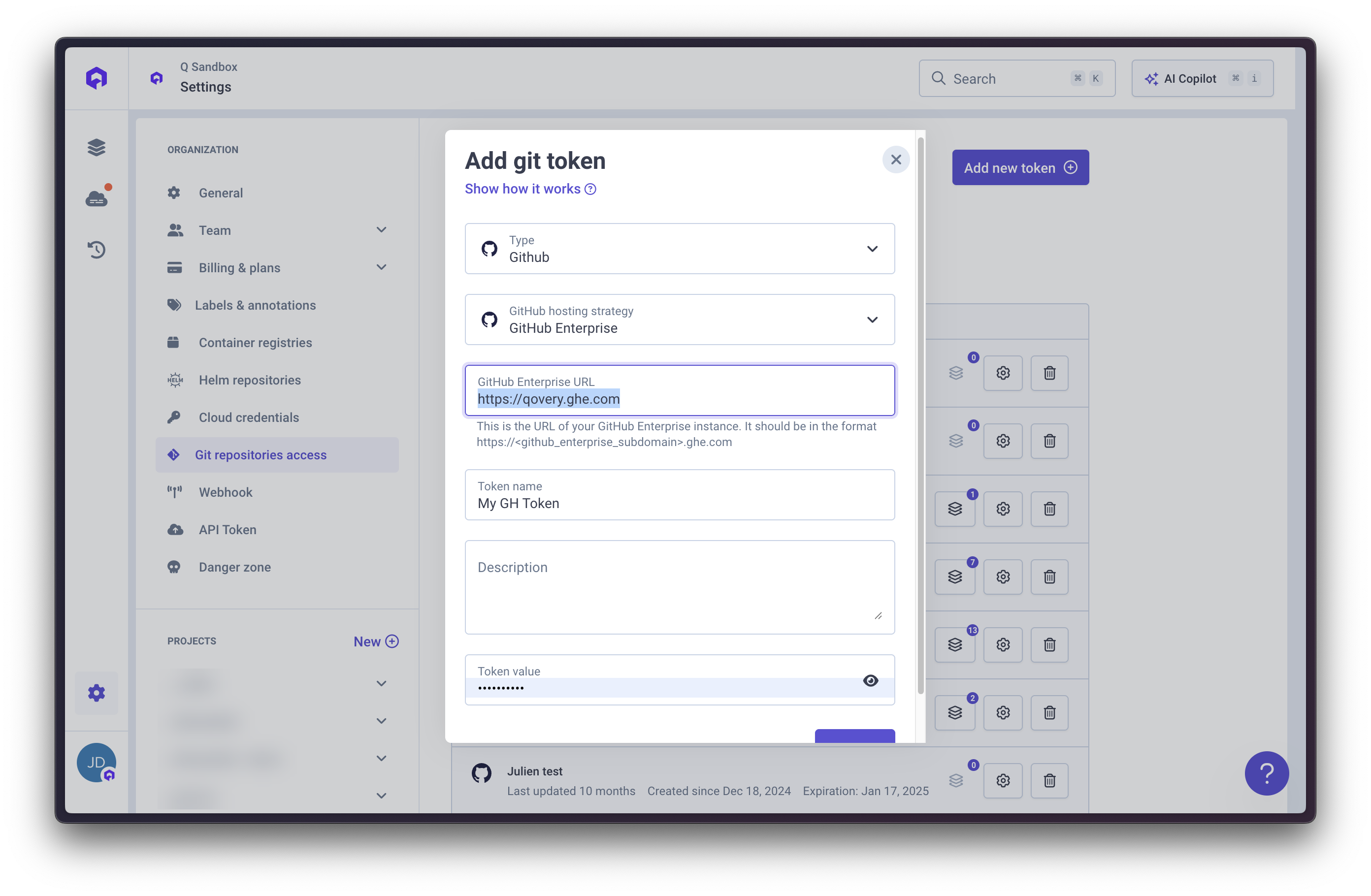
Once you’ve created a token in your Git provider, manage it in Qovery:Create the Token
Navigate to Git Repository Access
Open the
Git Repository Access section within organization settingsConfigure Token
Provide:
- Git Provider: Select GitHub, GitLab, or Bitbucket
- Name: Descriptive name (e.g., “GitHub Main Org”)
- Token: Paste your Git provider access token
- URL (for self-hosted only): Your Git server URL
- Workspace (for Bitbucket only): Your Bitbucket workspace name
Only users with Owner, Admin, or DevOps roles can manage Git tokens.
Using the Token
Once configured, Git tokens are automatically used when:- Creating new applications or services from Git repositories
- Cloning repository code during builds
- Monitoring repository changes for auto-deployment
- Accessing Dockerfile and build context
- Configuring webhooks for auto-deploy and preview environments
- Choose Git Repository as the source
- Select Organization Token (instead of personal Git account)
- Choose the Git provider type
- Select repository and branch
Update the Token
Updating a token affects all applications using repositories from this Git provider connection.
Delete the Token
To remove a Git token:- Locate the token in the Git Repository Access list
- Click the Delete button (trash icon)
- Confirm deletion
Deprecated: Qovery GitHub App
The legacy Qovery GitHub App provided GitHub repository access through an OAuth app. While still functional for existing users, new users should use Git tokens instead.Migration Recommendation
- Create GitHub personal access token (see instructions above)
- Add token to Qovery organization settings
- Update applications to use organization token instead of GitHub App
- Uninstall Qovery GitHub App once migration is complete
Best Practices
Use Organization Tokens
Use Organization Tokens
Use organizational Git tokens instead of personal accounts for better security and to decouple deployments from individual user access.
Set Token Expiration
Set Token Expiration
Always set an expiration date (90 days to 1 year) and set reminders for token rotation.
Use Dedicated Service Accounts
Use Dedicated Service Accounts
Create dedicated Git accounts for Qovery integration that aren’t tied to individual developers.
Descriptive Naming
Descriptive Naming
Use clear names like
github-main-org-production or gitlab-team-alpha to identify tokens easily.Regular Token Rotation
Regular Token Rotation
Rotate tokens periodically for security:
- Create new token with same permissions
- Update in Qovery
- Test with deployment
- Revoke old token