Prerequisites
- A Qovery cluster running on AWS EKS
- Basic knowledge of AWS IAM and Kubernetes
- Access to AWS Console and Qovery Console
Step 1: Create an Application Requiring S3 Permissions
First, deploy a simple Debian container that will need S3 access:- Deploy a Debian container with 1 instance and 128MB memory
- You can also use existing applications, containers, or jobs
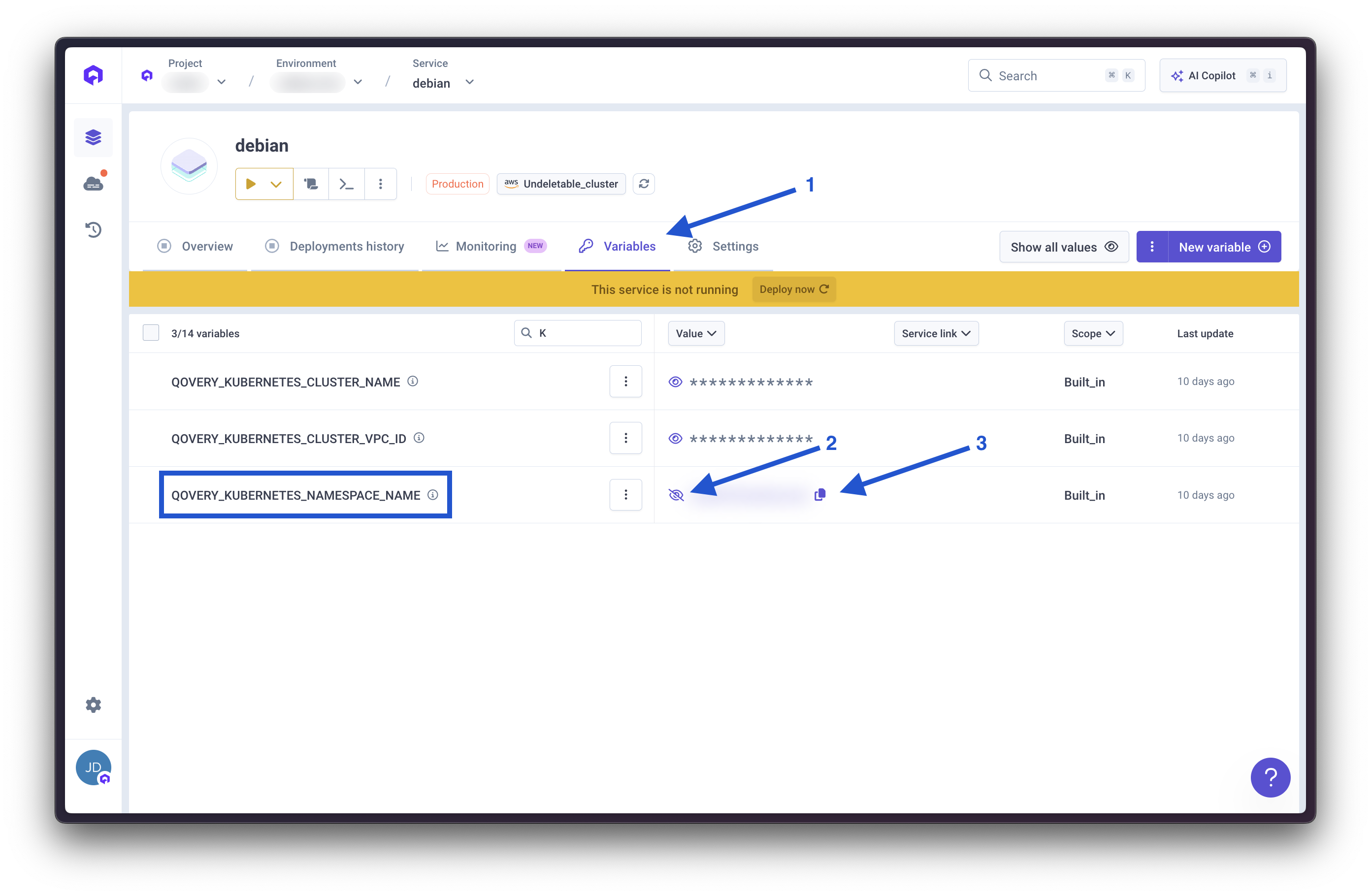
Get Kubernetes Namespace Name
- Access your container variables
- Locate
QOVERY_KUBERNETES_NAMESPACE_NAME - This value represents the namespace where the container runs
Step 2: Configure OIDC Provider
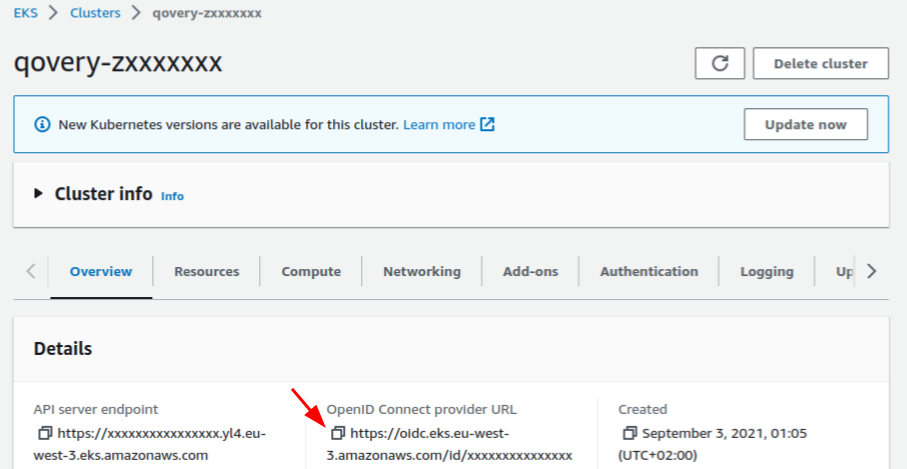
###Get Cluster OIDC Provider URL- Navigate to your AWS EKS cluster Overview section
- Copy the OpenID Connect provider URL
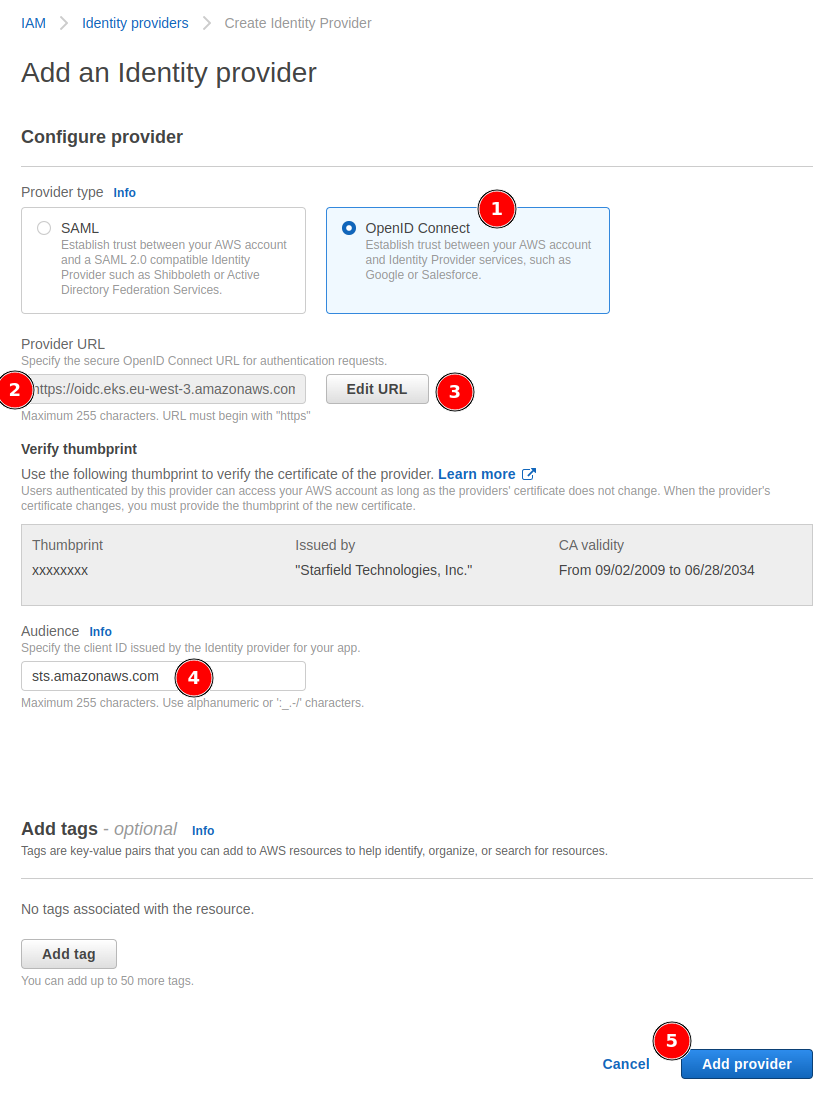
Create Identity Provider
- In AWS IAM, access the Identity providers section
- Select OpenID Connect provider type
- Paste the provider URL
- Click Get thumbprint
- Add
sts.amazonaws.comas Audience - Create the provider
Step 3: Configure AWS IAM Roles
Create a Role
- In IAM Roles section, select Create role
- Choose Web identity as Trusted entity type
- Set Identity provider and Audience to
sts.amazonaws.com

Add Role Permissions
- Select the desired policy (example uses
AmazonS3ReadOnlyAccess) - Set role name and description
- Proceed to creation
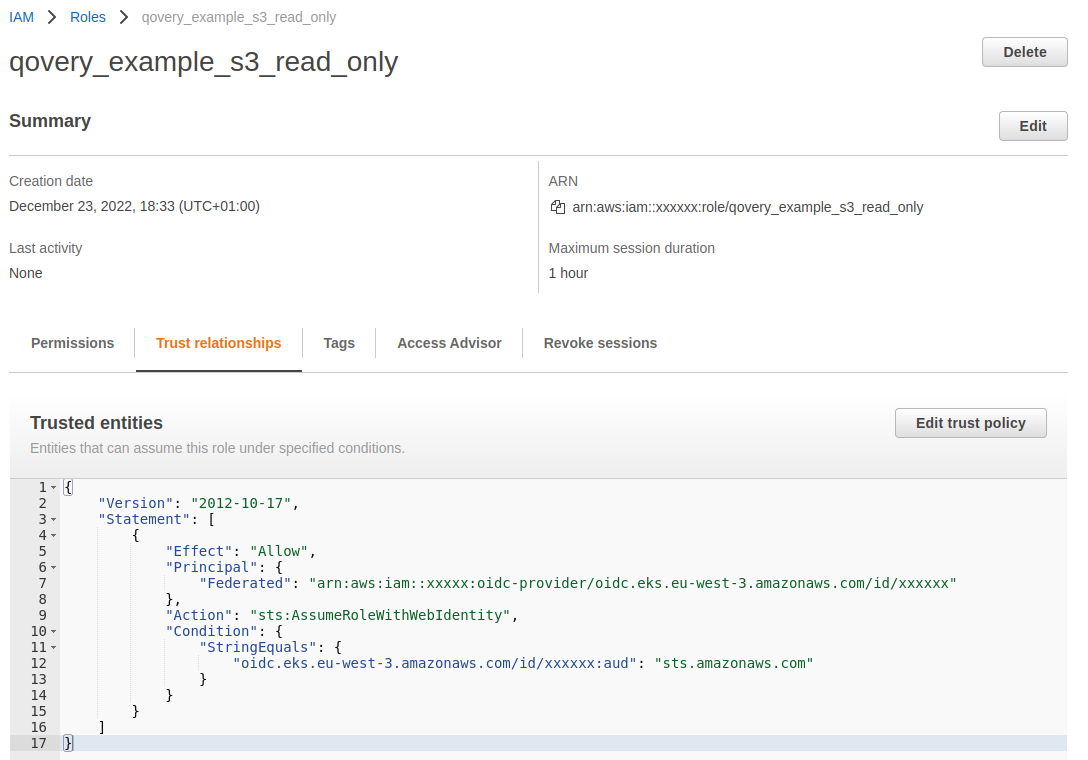
Configure Trusted Entities
- Environment-Scoped Role
- Cluster-Scoped Role
Update the trust policy from:To:Replace placeholders:
kubernetes_namespace: Your Qovery environment namespaceservice_account_name: Define a service account name (e.g.,my-s3-role)
Step 4: Create a Service Account
Service Account Manifest
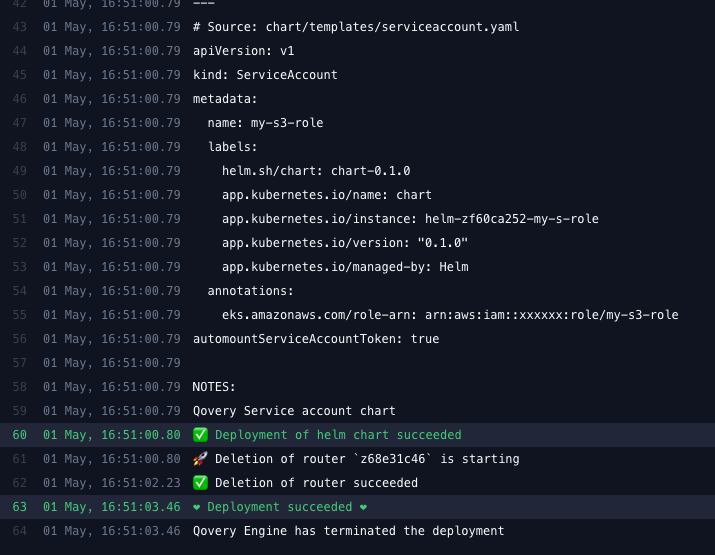
Deploy with Helm
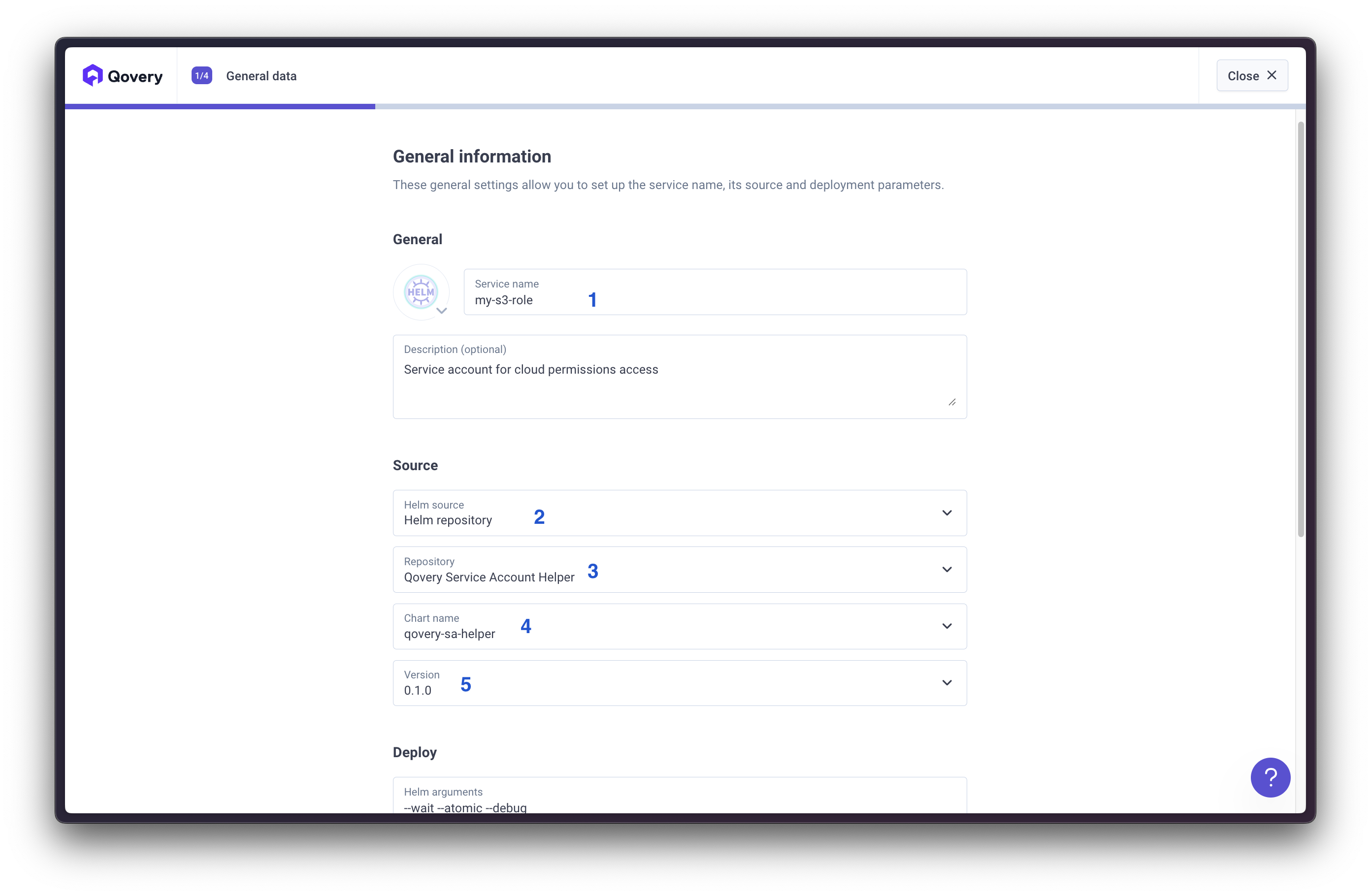
We’ll use a Helm chart to deploy the service account: Chart Configuration:- Helm source: Helm repository
- Chart name:
qovery-sa-helper - Version:
0.1.0
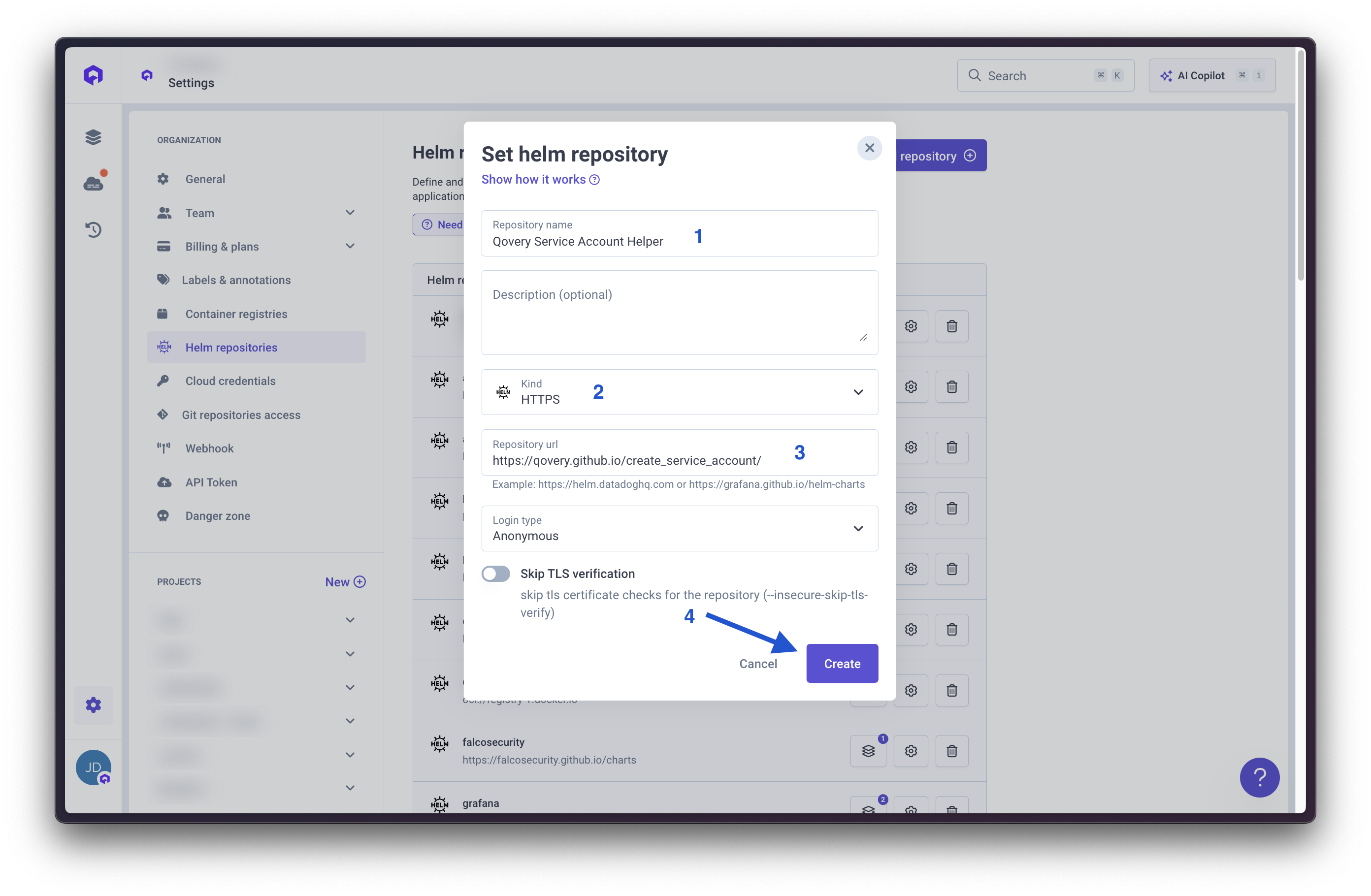
- Repository name:
Qovery Service Account Helper - Kind:
HTTPS - URL:
https://qovery.github.io/create_service_account/
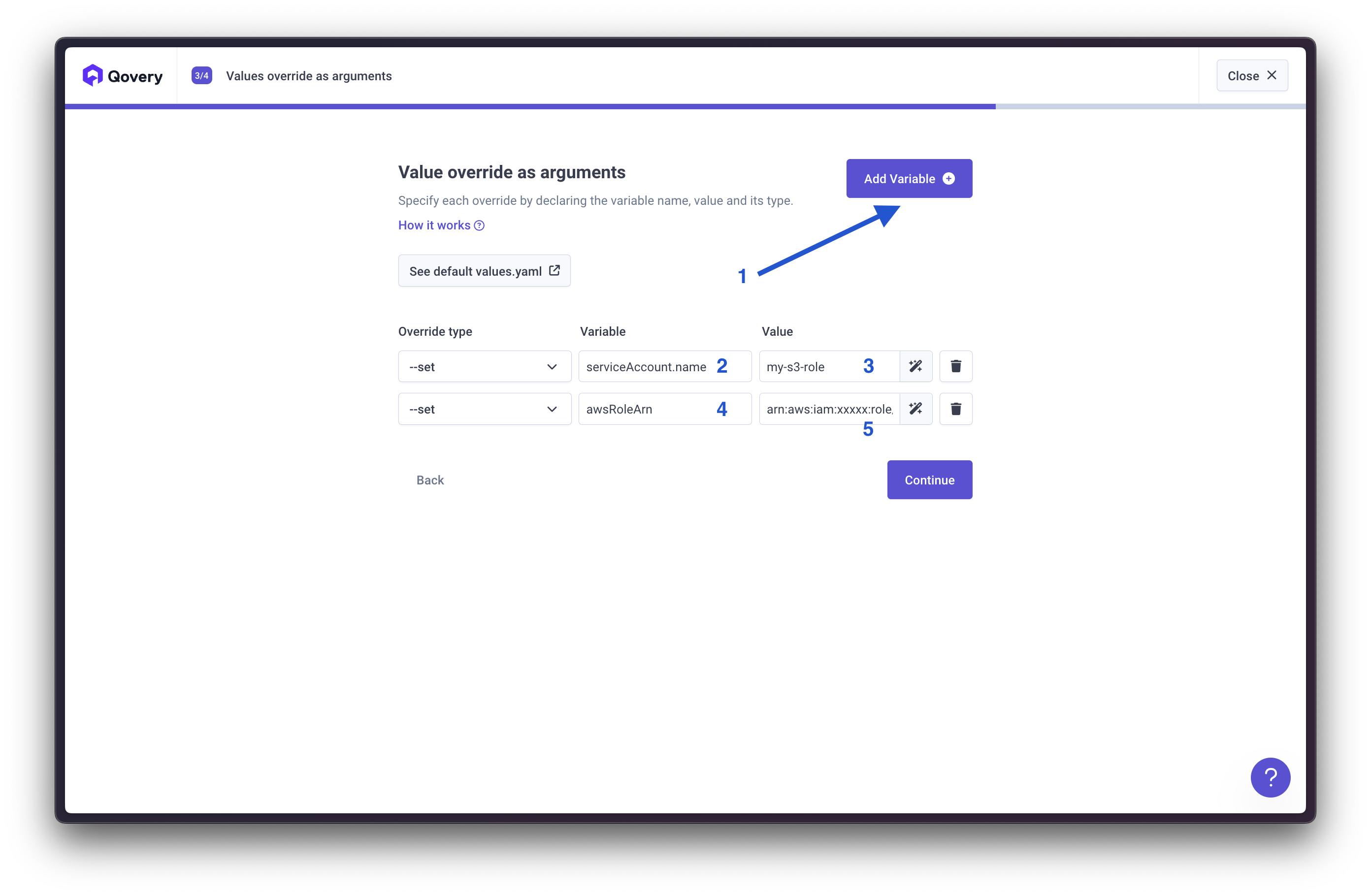
serviceAccount.name: Your service account nameawsRoleArn: Your role ARN

Step 5: Set Application Service Account
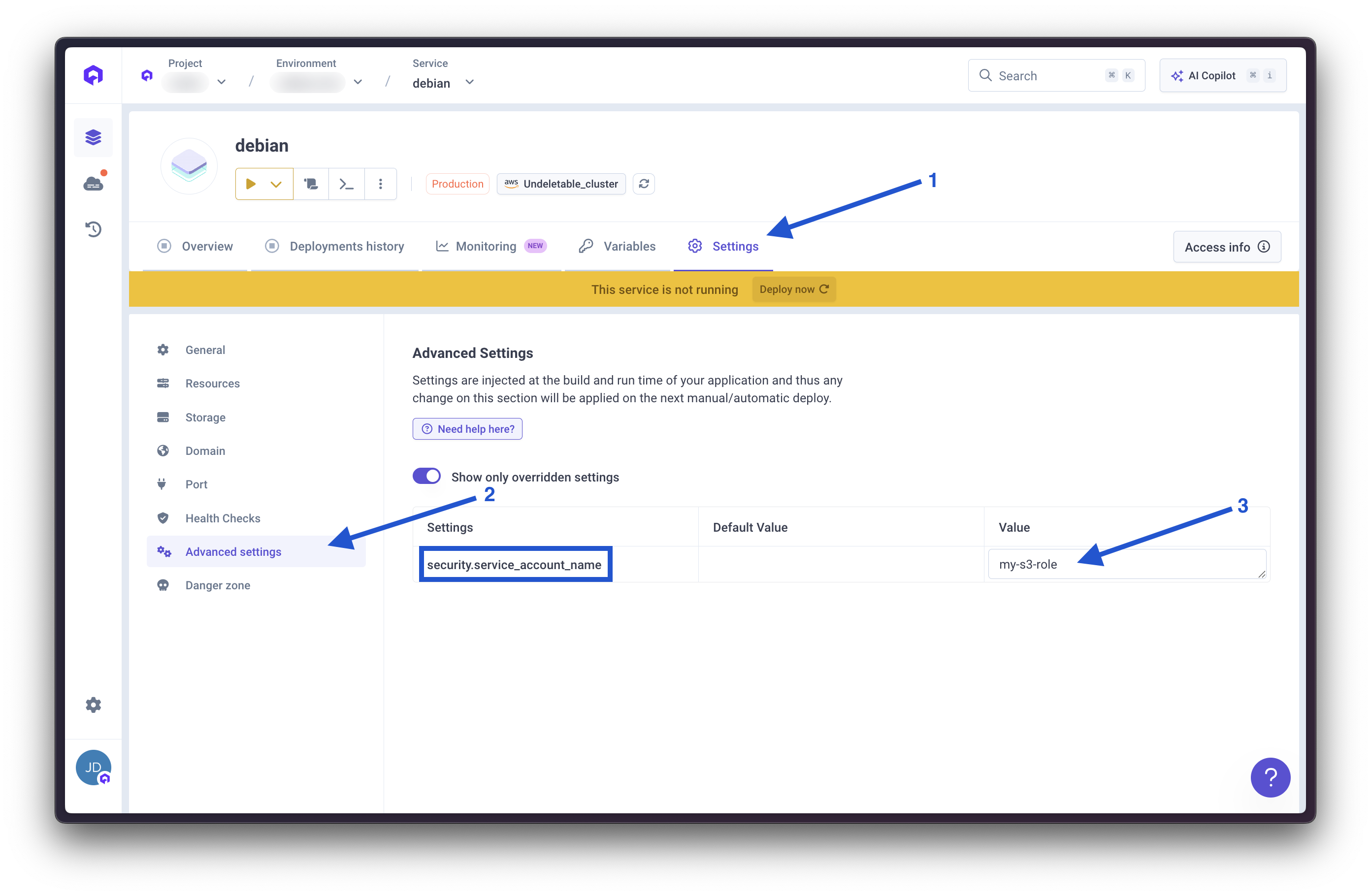
Configure Service Account
- Access your application Advanced settings
- Set Service account to the created service account name
- Deploy using the Deploy now button
Validate Access
Using Qovery CLI:Key Concepts
- OIDC Integration: Enables Kubernetes service accounts to assume AWS roles
- Token Rotation: Automatic credential rotation without manual management
- Namespace Scoping: Restricts role access to specific Kubernetes namespaces
- Cluster-Wide Availability: Service accounts accessible by all applications in the same namespace

