The Challenge
Single ingress controller approach creates problems:- Certificate generation failures affecting all domains if one validation fails
- Entire deployment risks from misconfigured domains
- Privacy issues: customers see other tenants’ domains in SSL certificates
- Let’s Encrypt rate limit concerns with many domains
The Solution: Dedicated Ingresses Per Tenant
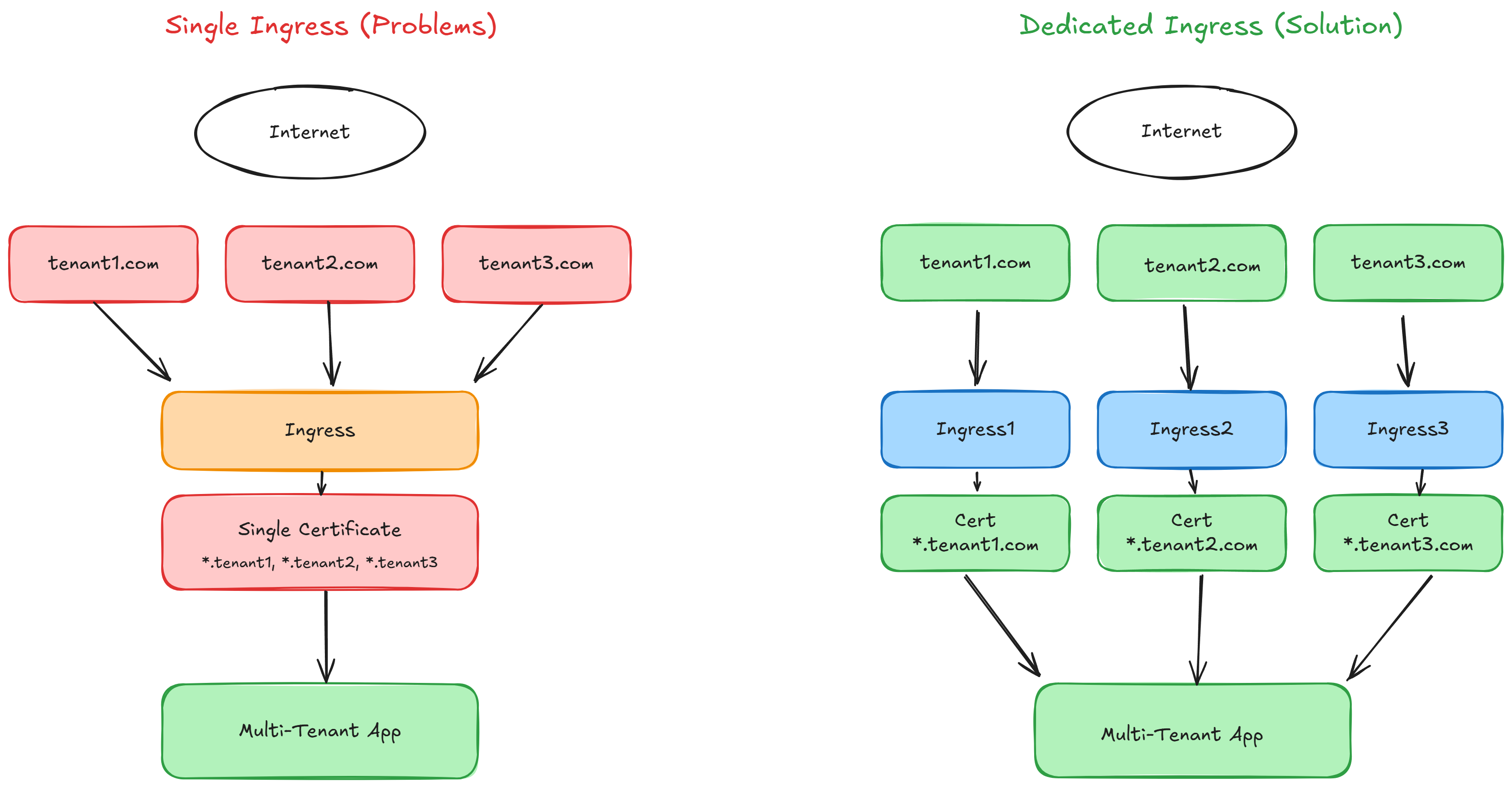
Benefits
- Isolation: Tenant certificate/ingress separation
- Reliability: One tenant’s issues won’t cascade to others
- Privacy: Certificates contain only specific tenant domains
- Scalability: Improved rate limit and renewal management
Prerequisites
- Qovery account with configured cluster
- DNS management access
- Basic understanding of Kubernetes ingress
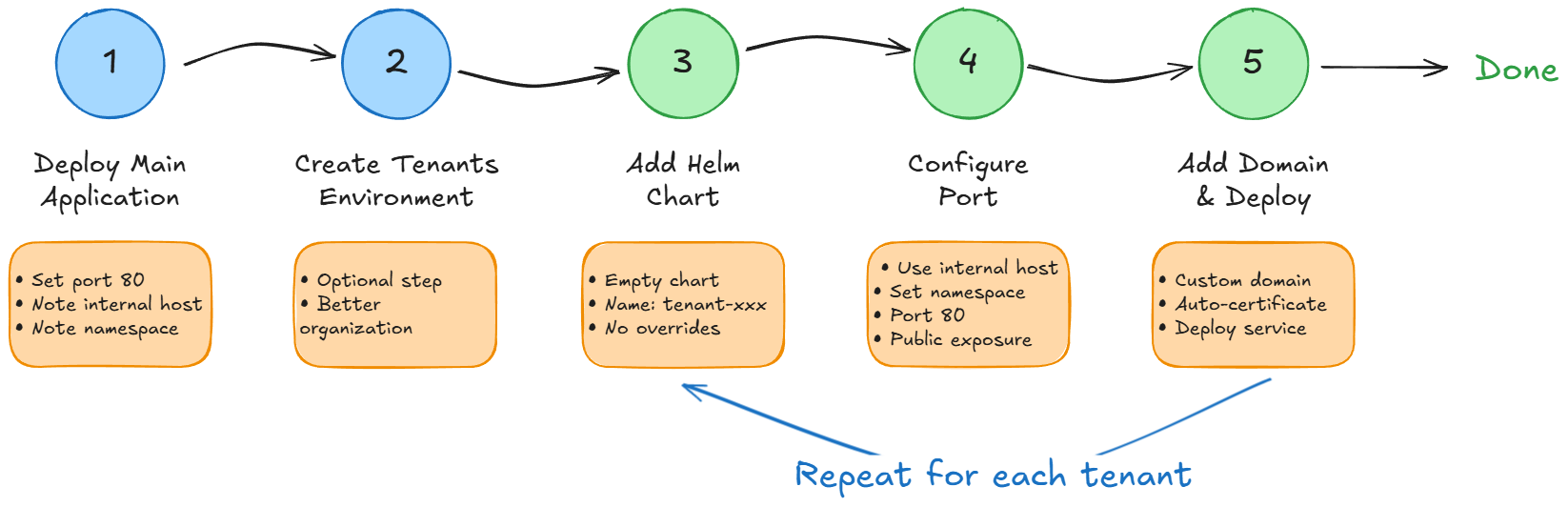
Implementation Guide
Step 1: Organize Your Platform (Optional)
Create separate environments for better organization:- Core Environment – Main application components (frontend, API, database)
- Tenants Environment – Tenant-specific ingress configurations
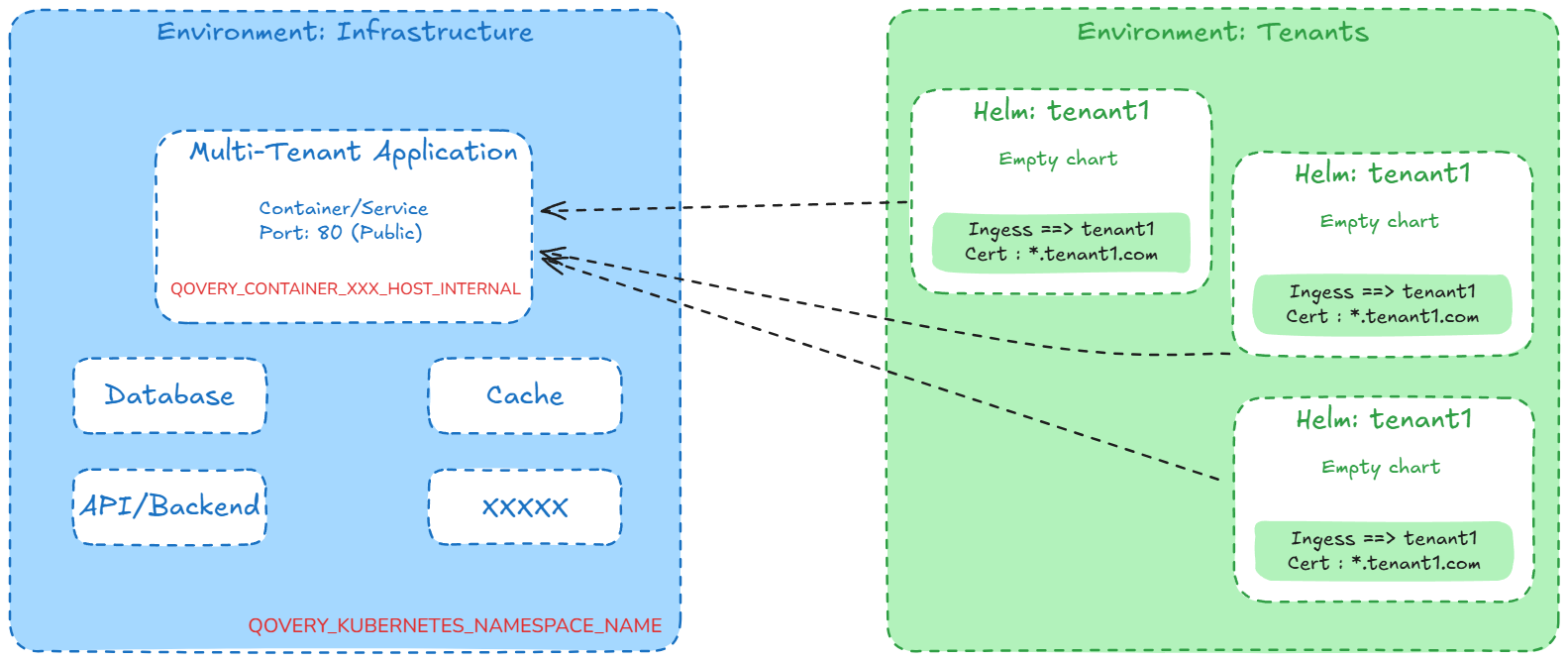
Separating core and tenant environments makes it easier to manage and scale your multi-tenant architecture.
Step 2: Deploy Your Main Application
Deploy Container
Deploy your application via UI, CLI, Terraform, or REST API to the Core environment.
Step 3: Create Tenant-Specific Ingresses
Create New Helm Service
- Create a new Helm service
- Use an empty chart template (or create a minimal chart)
- Name it after your tenant (e.g.,
tenant-acme-corp)
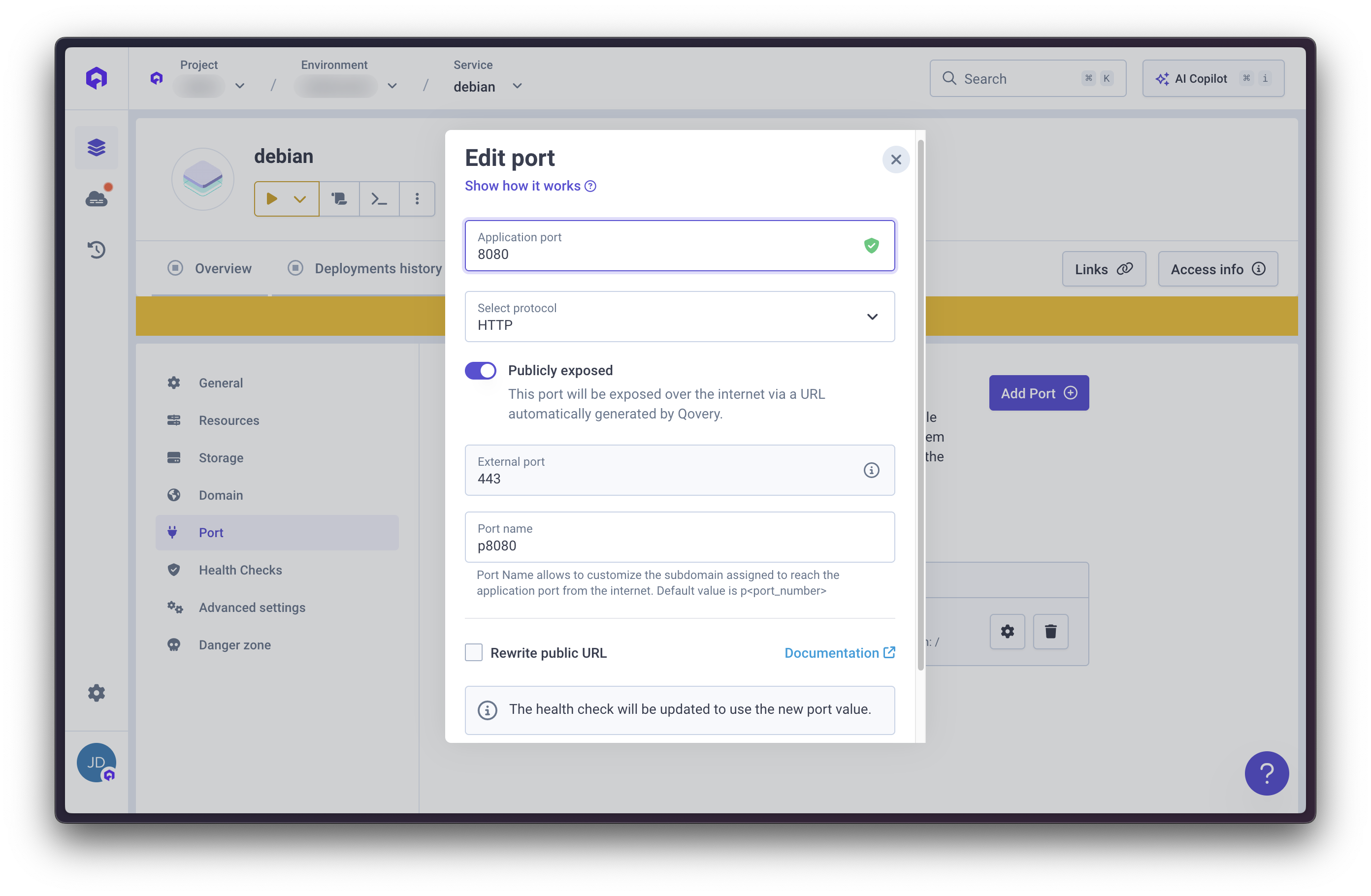
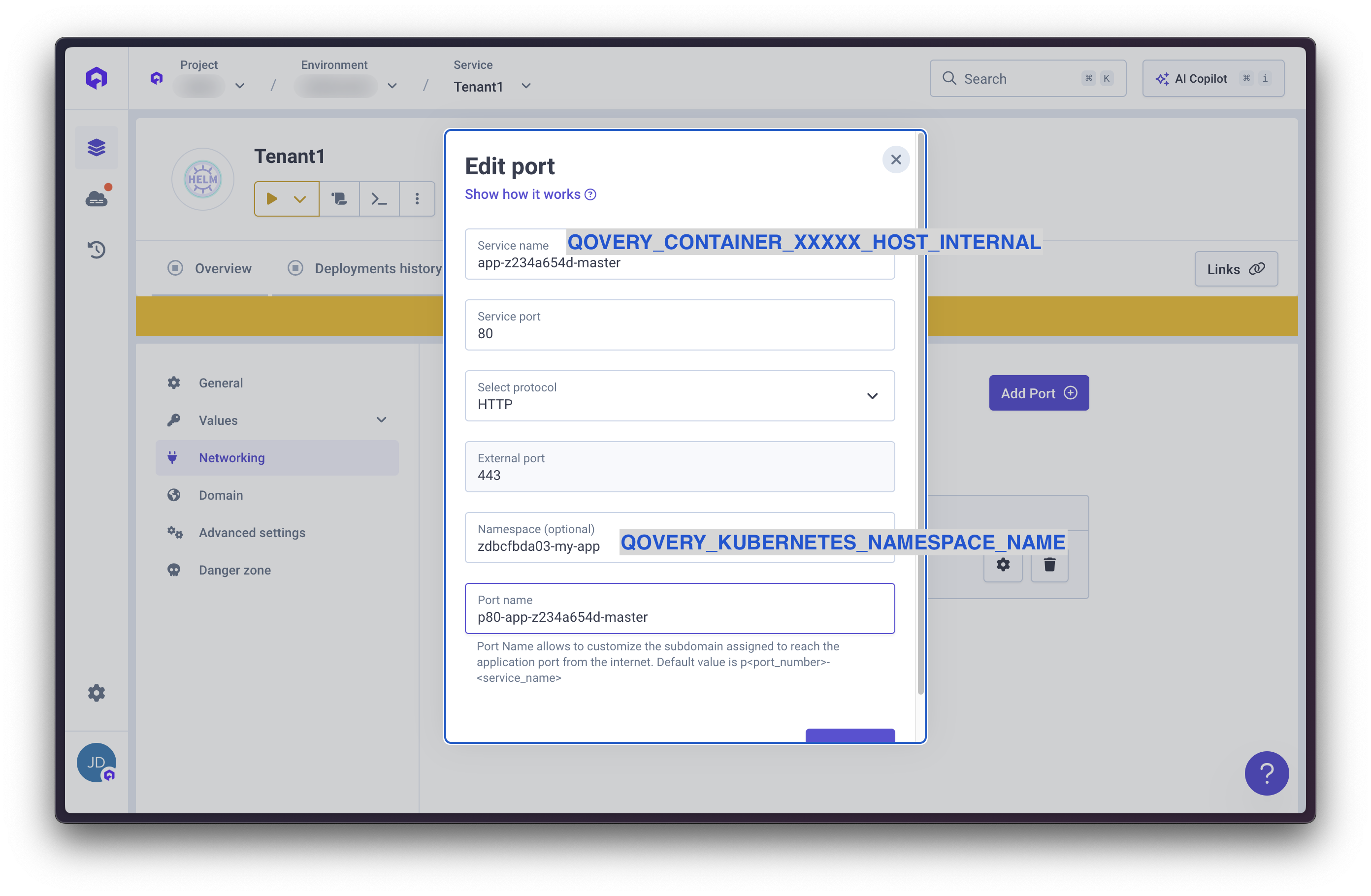
Configure Ingress Port
- Go to Settings → Ports
- Configure:
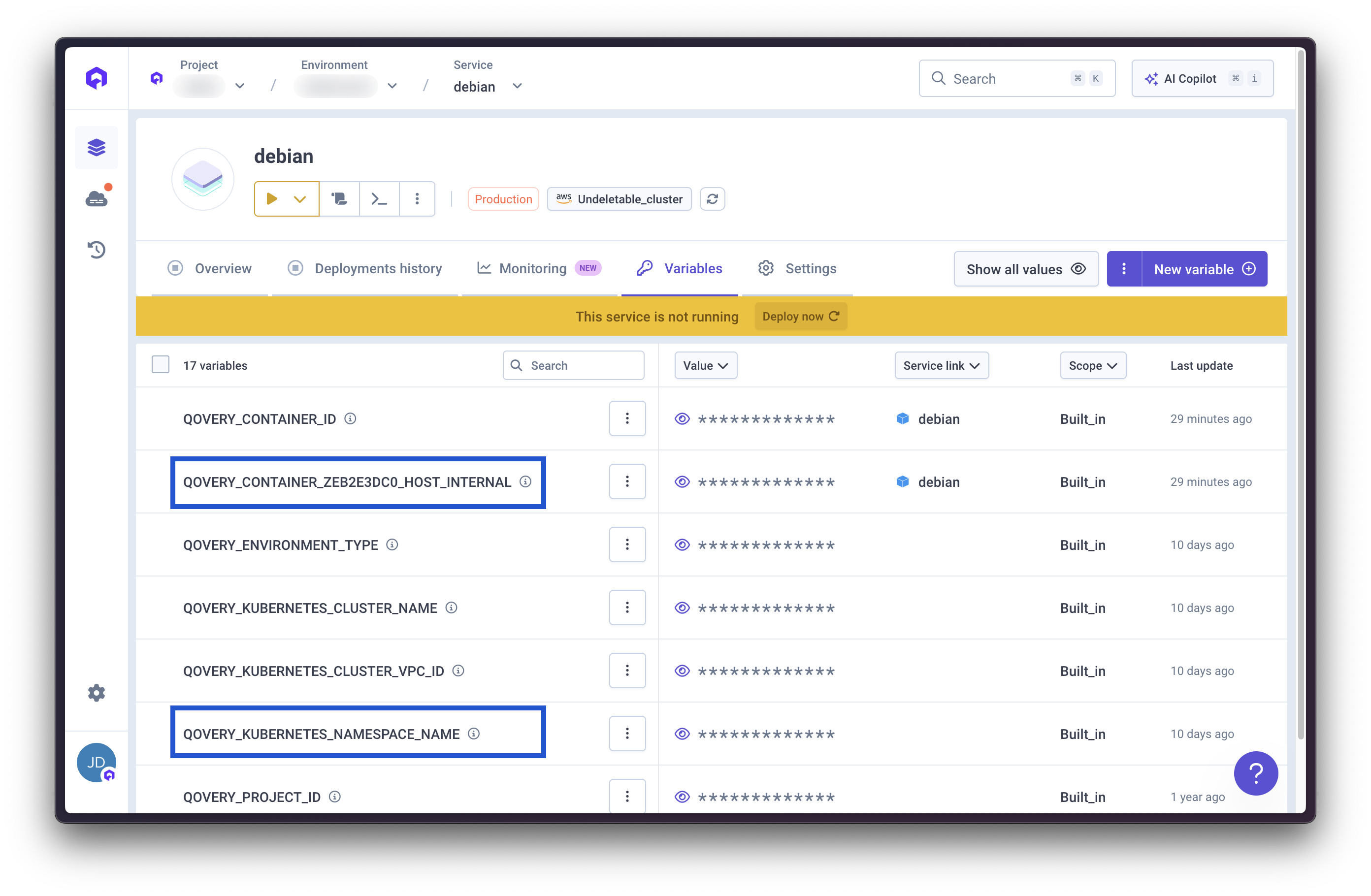
- Service name: Internal hostname from core application
- Service port: Core application’s port number
- Namespace: Kubernetes namespace from core application
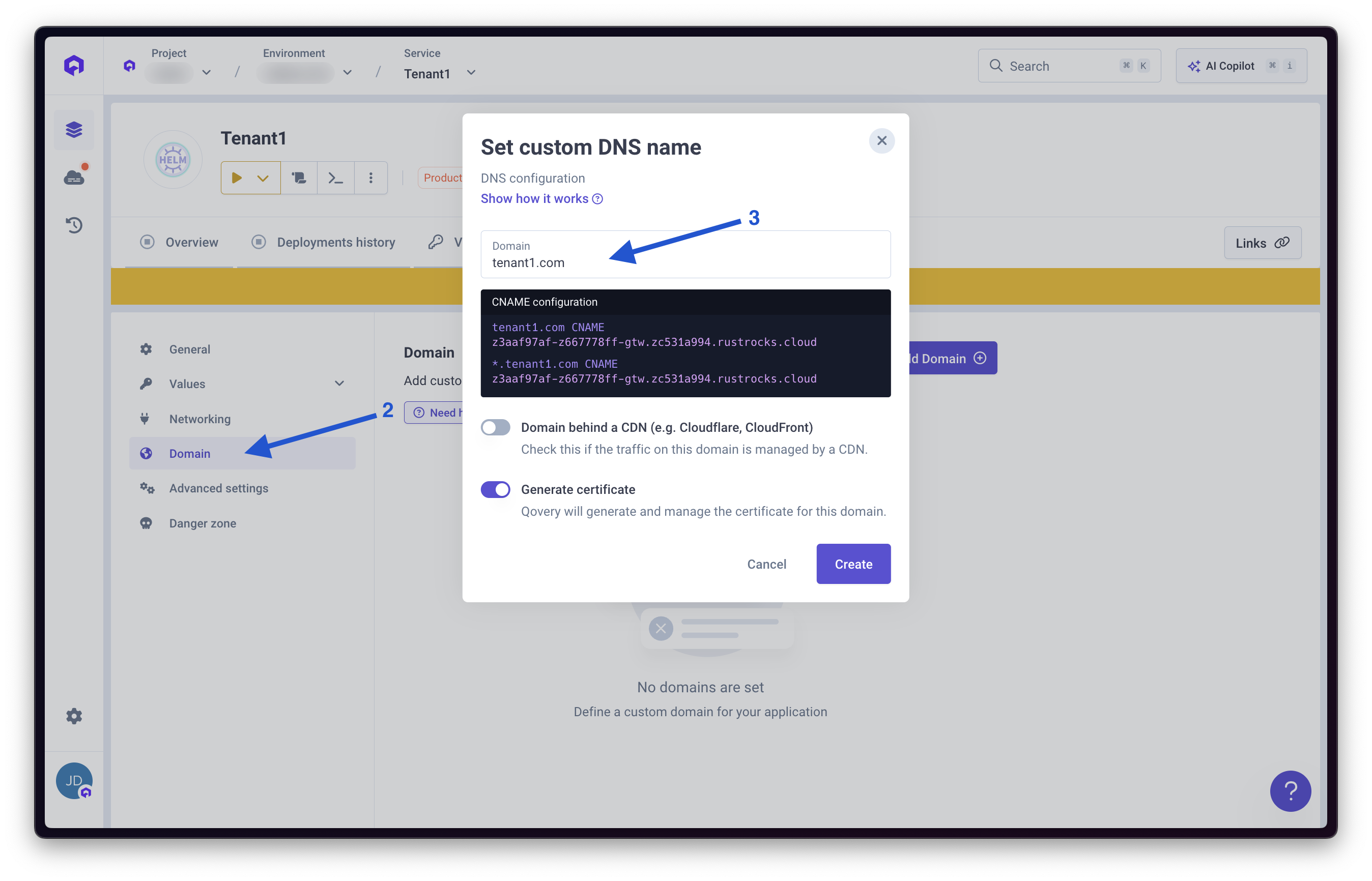
Add Tenant Custom Domain
- Go to Settings → Domains
- Add the tenant’s custom domain (e.g.,
acme-corp.example.com)
Step 4: Scale to Multiple Tenants
Options for adding more tenants:-
Clone Existing Configuration:
- Clone the tenant Helm service
- Update the custom domain
- Deploy
-
Create from Scratch:
- Repeat Step 3 for each new tenant
- Each tenant gets isolated ingress and certificate
Troubleshooting
Certificate Generation Issues
Certificate Generation Issues
Problem: SSL certificate not generating for tenant domainSolutions:
- Check DNS propagation:
dig _acme-challenge.tenant-domain.com CNAME - Verify CNAME record points to Qovery cluster
- Check ingress configuration in deployment logs
- Monitor cert-manager logs for certificate generation details
- Ensure domain is not behind CDN (or configure properly)
Routing Issues
Routing Issues
Problem: Traffic not reaching the applicationSolutions:
- Verify internal service name matches application hostname
- Confirm namespace configuration for multi-environment setups
- Check that core application is running and healthy
- Review ingress logs for routing errors
- Test internal connectivity between namespaces
Rate Limiting
Rate Limiting
Problem: Hit Let’s Encrypt rate limitsSolutions:
- Use Let’s Encrypt staging environment for testing
- Implement certificate caching
- Stagger tenant onboarding to spread certificate requests
- Consider using wildcard certificates for subdomains
Performance Issues
Performance Issues
Problem: Slow response times for tenant requestsSolutions:
- Check ingress controller resource allocation
- Monitor core application performance
- Review network policies
- Consider scaling ingress controller replicas
- Implement caching at CDN or application level
Advanced Configurations
Wildcard Certificates
For subdomains under a single domain:Custom Certificate Providers
Use custom certificate issuers:Automatic Tenant Provisioning
Use Qovery API to automate tenant creation:Security Considerations
Tenant Isolation
Tenant Isolation
- Each tenant has dedicated ingress
- SSL certificates are tenant-specific
- No cross-tenant certificate exposure
- Network policies can further isolate traffic
Certificate Management
Certificate Management
- Automatic renewal before expiration
- Failed renewals don’t affect other tenants
- Certificate rotation without downtime
- Private keys never shared between tenants
Access Control
Access Control
- Use RBAC to control who can add tenants
- Audit logs track tenant creation
- Separate environments limit blast radius
- API tokens for automated provisioning
Monitoring and Maintenance
Key Metrics to Monitor
- Certificate expiration dates
- Certificate generation success rate
- Ingress response times
- Error rates per tenant
- SSL/TLS handshake failures
Automated Alerts
Set up alerts for:- Certificate generation failures
- Certificates expiring within 30 days
- Ingress health check failures
- High error rates for specific tenants
Conclusion
Dedicated ingresses create a robust, scalable, and secure multi-tenant architecture with:- Better tenant isolation
- Easier troubleshooting
- Improved customer privacy
- Reduced rate limit concerns
- Independent certificate lifecycle management