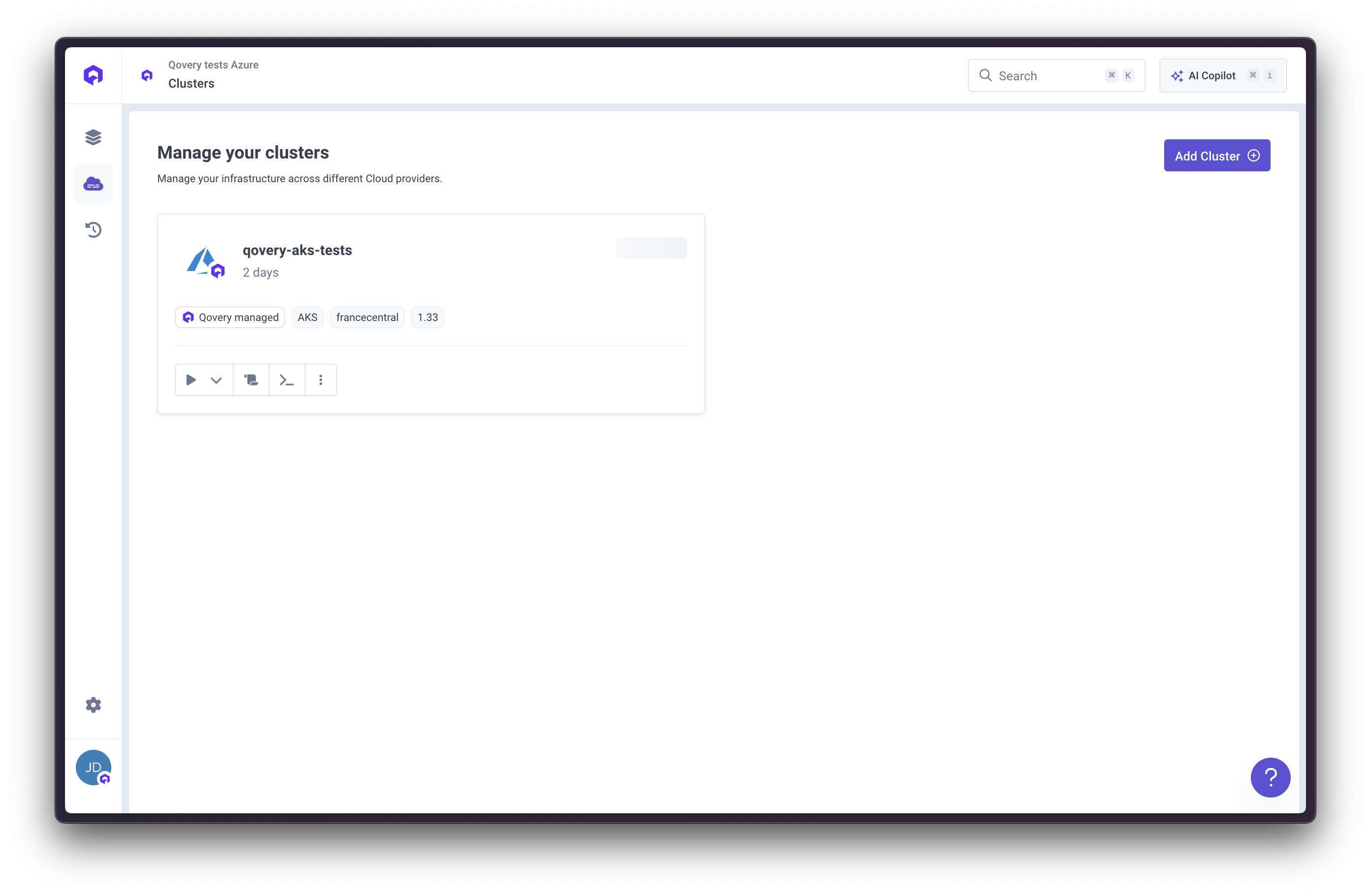
Overview
Qovery simplifies Azure Kubernetes Service (AKS) management by:- Automating cluster creation and configuration
- Managing networking, load balancers, and DNS
- Providing built-in monitoring and logging
- Handling rolling updates and scaling
- Securing your infrastructure with best practices
Fully Managed
Qovery creates and manages your AKS cluster automatically
Production Ready
Best practices for security, networking, and reliability
Auto-Scaling
Automatic node scaling based on workload
Multi-Region
Deploy across Azure regions worldwide
Prerequisites
Before you begin, ensure you have:Azure Account: Active Azure subscription with admin access
Azure Tenant: Access to an Azure Active Directory tenant
Qovery Account: Free account at console.qovery.com
Permissions: Ability to create service principals and assign roles
Required Azure Permissions
Your Azure account needs these permissions:- Create and manage AKS clusters
- Create service principals
- Assign contributor role
- Manage virtual networks
- Create resource groups
Step 1: Create Azure Credentials
Qovery needs credentials to manage resources in your Azure subscription. We use a secure service principal approach that avoids storing long-lived credentials.Get Your Azure IDs
Find Tenant ID
- Go to Azure Portal
- Navigate to Azure Active Directory
- Click Overview in the left sidebar
- Copy your Tenant ID (also called Directory ID)
Find Subscription ID
- In Azure Portal, go to Subscriptions
- Click on the subscription you want to use
- Copy the Subscription ID from the overview page
Generate Installation Command
Start Cluster Creation
- Go to Qovery Console
- Click Clusters in the left sidebar
- Click Create Cluster
- Select Azure as the cloud provider
Enter Azure Details
- Enter your Tenant ID
- Enter your Subscription ID
- Click Next
Run Installation Script
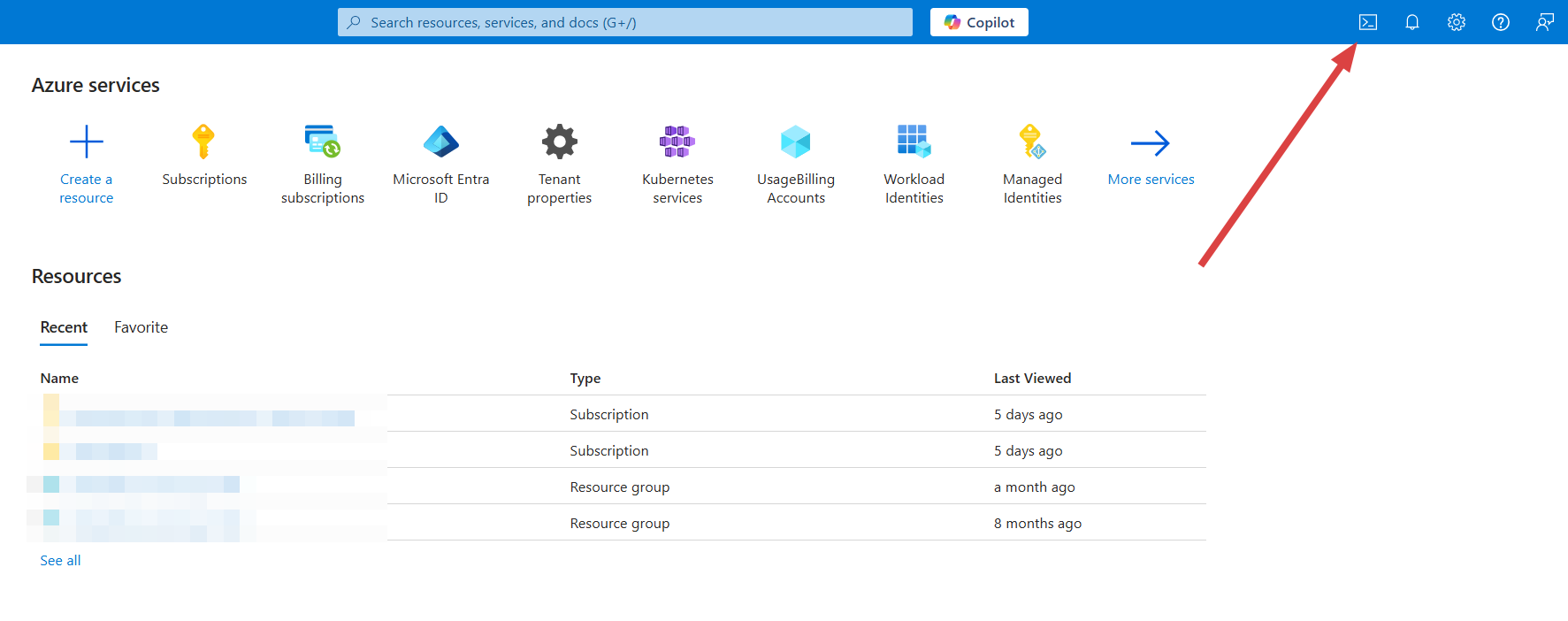
Open Azure Cloud Shell
- In Azure Portal, click the Cloud Shell icon (>_) in the top navigation bar
-
Important: Select Bash mode (not PowerShell)
Run the Command
- Paste the command from Qovery into Azure Cloud Shell
- Press Enter
- Review the subscription details displayed
- The script will create a service principal and assign necessary permissions
Source: Content above is maintained in
/snippets/azure-credentials.mdx. Update snippet first, then copy to all usage locations.Step 2: Configure Your Cluster
Now configure your AKS cluster settings in the Qovery console.Basic Configuration
Cluster Name
Choose a descriptive name for your cluster:
production-aksstaging-azuredev-aks-eastus
Select Region
Choose an Azure region closest to your users:North America:
eastus- East US (Virginia)eastus2- East US 2 (Virginia)westus2- West US 2 (Washington)centralus- Central US (Iowa)
westeurope- West Europe (Netherlands)northeurope- North Europe (Ireland)uksouth- UK South (London)francecentral- France Central (Paris)
southeastasia- Southeast Asia (Singapore)eastasia- East Asia (Hong Kong)japaneast- Japan East (Tokyo)australiaeast- Australia East (Sydney)
Choose a region that complies with your data residency requirements.
Node Pool Configuration
Configure the VM sizes for your AKS node pools:VM Size Recommendations
VM Size Recommendations
Development/Testing:
Standard_B2s(2 vCPU, 4GB RAM)Standard_B2ms(2 vCPU, 8GB RAM)
Standard_D2s_v3(2 vCPU, 8GB RAM)Standard_D4s_v3(4 vCPU, 16GB RAM)Standard_D8s_v3(8 vCPU, 32GB RAM)
Standard_F2s_v2(2 vCPU, 4GB RAM)Standard_F4s_v2(4 vCPU, 8GB RAM)
Standard_E2s_v3(2 vCPU, 16GB RAM)Standard_E4s_v3(4 vCPU, 32GB RAM)
Networking Configuration
Qovery automatically configures Azure networking: What’s Created:- Virtual Network (VNet) with CIDR
10.0.0.0/16 - Public subnet for load balancers
- Private subnets for nodes
- NAT Gateway for outbound internet access
- Network Security Groups (NSGs)
- Azure Load Balancer for ingress
Advanced Networking Options
Advanced Networking Options
VNet Peering:
Configure VNet peering to connect to existing Azure resources (databases, storage, etc.).Custom CIDR:
Change the default VNet CIDR if it conflicts with your existing networks.Private Cluster:
Enable private cluster mode to remove public API endpoints (requires VPN or ExpressRoute).
Step 3: Deploy Your Cluster
Review Configuration
Review all your cluster settings:
- Cluster name
- Region
- VM sizes
- Networking options
Create and Deploy
Click Create and Deploy
You can start configuring applications immediately! The cluster will be available once deployment completes.
Monitor Progress
Watch the deployment progress in the Qovery console.Timeline:
- 0-5 min: Creating Azure resources (Resource Group, VNet, NSGs)
- 5-10 min: Provisioning AKS control plane
- 10-15 min: Creating node pools
- 15-20 min: Installing Qovery components (ingress, monitoring, etc.)
- 🟡 Creating: Infrastructure provisioning in progress
- 🟢 Running: Cluster is ready to use
- 🔴 Error: Check logs for troubleshooting
What Gets Created
Qovery automatically provisions these Azure resources:Core Infrastructure
Core Infrastructure
- Resource Group: Dedicated group for all cluster resources
- AKS Cluster: Managed Kubernetes cluster
- Virtual Network: Isolated network for your cluster
- Subnets: Public and private subnets
- NAT Gateway: Outbound internet connectivity
- Network Security Groups: Firewall rules
Networking
Networking
- Azure Load Balancer: Layer 4 load balancing
- Application Gateway (optional): Layer 7 load balancing
- Public IP Addresses: For ingress traffic
- Private DNS Zone: Internal service discovery
Compute
Compute
- Virtual Machine Scale Sets: Auto-scaling node pools
- Managed Disks: Persistent storage for nodes
- System Node Pool: Kubernetes system components
- User Node Pools: Your application workloads
Qovery Components
Qovery Components
- NGINX Ingress Controller: HTTP/HTTPS routing
- Cert-Manager: Automatic SSL/TLS certificates
- Qovery Agent: Cluster management
- Monitoring Stack: Metrics and logging
- DNS Management: Automatic domain configuration
Post-Installation Steps
Once your cluster is running:Deploy Your First Application
Follow the Deploy Your First App guide
Set Up Monitoring
Configure Azure Monitor or Datadog
Troubleshooting
Credential Creation Failed
Credential Creation Failed
Error: “Failed to create service principal”Solutions:
- Verify you have permissions to create service principals
- Check that your Azure subscription is active
- Ensure you’re using Bash mode (not PowerShell) in Cloud Shell
- Verify Tenant ID and Subscription ID are correct
Cluster Creation Stuck
Cluster Creation Stuck
Issue: Cluster stuck in “Creating” state for over 30 minutesSolutions:
- Check Azure quotas for your subscription (vCPUs, Public IPs)
- Verify the selected region has capacity
- Check Azure status page for outages
- Contact Qovery support if issue persists
Insufficient Quota
Insufficient Quota
Error: “Quota exceeded for resource”Solutions:
- Check your Azure quotas: portal.azure.com/#view/Microsoft_Azure_Capacity/QuotaMenuBlade
- Request quota increase through Azure Portal
- Choose a different VM size or region
- Reduce the number of nodes
- Total Regional vCPUs
- VM family specific vCPUs (D-series, F-series, etc.)
- Public IP addresses
- Load balancers
Network Configuration Issues
Network Configuration Issues
Issue: Applications can’t access external servicesSolutions:
- Verify NAT Gateway is properly configured
- Check Network Security Group rules
- Ensure subnet routing tables are correct
- Test connectivity from a pod:
kubectl run -it debug --image=nicolaka/netshoot --rm
Advanced Configuration
Private Cluster Mode
For enhanced security, enable private cluster mode:VNet Peering
Connect your AKS cluster to existing Azure resources:- Create VNet peering from Qovery VNet to your VNet
- Configure route tables
- Update Network Security Groups
- Test connectivity
Custom DNS
Use your own DNS servers:- Configure custom DNS in VNet settings
- Update CoreDNS configuration
- Test name resolution
Best Practices
Right-Size VMs
Start with smaller VMs and scale up based on actual usage patterns
Enable Monitoring
Configure Azure Monitor or third-party monitoring from day one
Implement RBAC
Use Azure AD integration and Kubernetes RBAC for access control
Regular Updates
Keep your AKS cluster updated with the latest Kubernetes versions
Backup Strategy
Implement automated backups for persistent data and configurations
Next Steps
Deploy Your First App
Complete step-by-step deployment guide
Configure RBAC
Set up team access control
Set Up CI/CD
Automate deployments with GitHub Actions or Azure DevOps
Monitor Your Cluster
Configure monitoring and alerting
Additional Resources
- Azure AKS Documentation
- Azure Pricing Calculator
- Qovery Status Page
- Qovery Community Forum - Updates and announcements from the Qovery team